A 20 person company was hit with a $90,000 loss through a fraudulent wire transfer to Russia. The person accessing the company’s (let’s call the company XYZ Corp) bank account used the login and password of a real XYZ employee. The employee’s credentials were compromised and used to authorize the wire transfer.
Here are some facts about the event:
- The credentials were real — nothing was faked
- This occurred through a major bank
- The bank did not cover the loss since a valid login was used to wire the funds
- XYZ could have prevented the fraudulent transfer
XYZ could have used two factor authentication (sometimes called multi-factor) to prevent the wire transfer. There are a few ways this could have been prevented — more on that later.
What is Two Factor Authentication?
Two factor authentication is when you use a login, password, and another code to authenticate your use of a system. The extra code is a second factor — thus two factor.
You may use two factor authentication for some online services like your health provider, email, or a work application. The most common method of two factor authentication is for an online service to ask you a series of questions such as “What was the name of your favorite pet?” Luckily, most websites have stopped using easily searchable info like your mother’s maiden name…

A better method of two factor authentication is to require an expiring code to be typed into a field. Medical offices tend to use these before other businesses due to the sensitivity of the information accessible from computers. The image, above, is from an RSA Key. The numbers in the key change every 30 seconds. A bad guy would have to have your login, password, and physical access to the RSA Key to compromise your account.
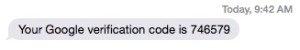
You may also see two factor authentication using a text message, an email, or an app on your phone to provide the expiring code. An example of the text message code is below.
Online Services Offering Two Factor Authentication
You can find a big list of online services, banks, email providers, and more at https://twofactorauth.org/
We suggest checking this website to make a To Do list for setting up two factor authentication if warranted. You may use one of the services or sites for non-critical info. There may be no point in setting up an extra layer of security for those services or sites.
How Else Could XYZ Protect Its Bank Account?
There are a few other methods of protection and notifications some banks offer.
After you turn on two factor authentication, here’s what we recommend:
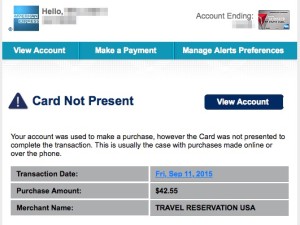
- Set up email and/or SMS alerts for transactions above a certain dollar amount and for “card not present” transactions.
- Contact your bank to let them know ACH transactions above a certain dollar amount are not allowed online.
- For credit cards, add email and/or SMS notifications for suspicious transactions.
- For bank accounts only, add a “low balance” notification and pick a dollar amount you know should always be in the account.
- Create a bank account(s) at your bank that remains separate from your main accounts. For example, if your business has an account for retained earnings then you can keep it from showing up when you log into your bank’s website. There’s no way to transfer from this account online if a bad guy never sees the account.
- Access your bank from a bookmark/favorite instead of typing it in. This prevents you from mis-typing and ending up on a malicious clone site.
- Set a calendar event to review all bank and credit card account users. Companies with multiple users should regularly audit the list to remove people who have changed positions or left the firm.
- Use a dedicated workstation to access your bank. We have clients do this and limit the machine’s access to only banking websites.
Your bank and credit card providers use sophisticated tools to monitor transactions for fraud and other suspicious activity. When you take these extra steps, you are increasing your protection in ways the banks’ systems cannot.